Metasploit is an open-source penetration testing framework used for developing, testing, and executing exploit code against remote targets. Developed by H.D. Moore in 2003, Metasploit provides a comprehensive suite of tools and utilities for security professionals and researchers to assess and exploit vulnerabilities in networks and systems.
Metasploit offers a vast database of known vulnerabilities, exploits, and payloads, allowing users to perform a wide range of security testing activities, including penetration testing, vulnerability assessment, and security research. It supports various exploitation techniques, from simple remote code execution to sophisticated privilege escalation and post-exploitation activities.
One of Metasploit’s key features is its modular architecture, which allows users to easily extend and customize its functionality through the use of modules. Modules can be written in Ruby or other programming languages, enabling developers to create custom exploits, payloads, auxiliary modules, and post-exploitation modules to suit their specific testing needs.
Metasploit also includes features for automating common penetration testing tasks, such as scanning for vulnerabilities, brute-forcing credentials, and conducting network reconnaissance. It provides a user-friendly command-line interface (CLI) as well as a web-based graphical interface (Metasploit Community Edition) for interacting with its features and conducting security assessments.
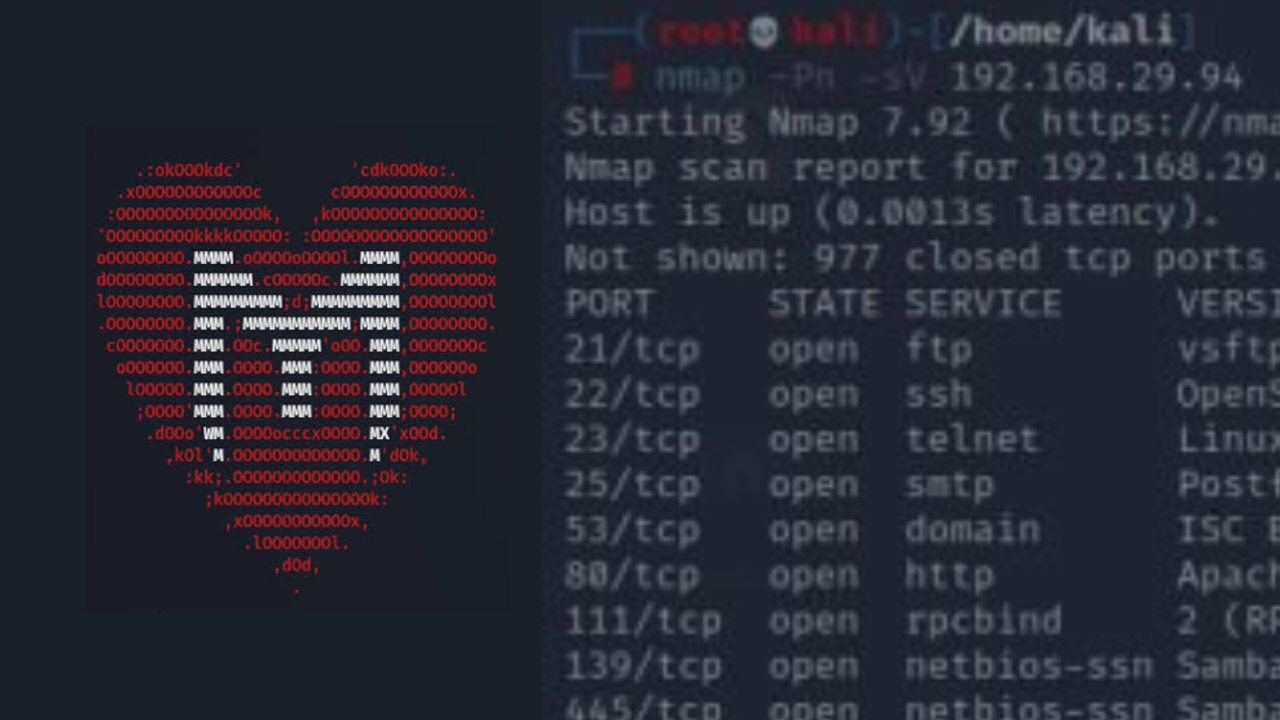
For example, to exploit a known vulnerability in a target system using Metasploit, security professionals can use the following steps:
1. Identify the target system and vulnerability.
2. Search for an appropriate exploit module in Metasploit’s database.
3. Configure the exploit module with target-specific parameters.
4. Execute the exploit to gain unauthorized access to the target system.
Metasploit’s comprehensive feature set, extensive database of vulnerabilities, and active community of contributors make it a valuable tool for security professionals engaged in offensive security testing and vulnerability research.
Metasploit – Explained In 200 Words