Ethical hacking, rooted in the 1960s, evolved alongside the growth of computer networks and cyber threats. Early practitioners, dubbed “white-hat hackers,” pioneered techniques to secure systems. In the 1970s and 1980s, ethical hacking gained prominence as organizations sought ways to safeguard their digital assets. The Computer Fraud and Abuse Act of 1986 in the UnitedContinue reading “Ethical Hacking – Explained In 200 Words”
Category Archives: Hacks and Features
Metasploit – Explained In 200 Words
Metasploit is an open-source penetration testing framework used for developing, testing, and executing exploit code against remote targets. Developed by H.D. Moore in 2003, Metasploit provides a comprehensive suite of tools and utilities for security professionals and researchers to assess and exploit vulnerabilities in networks and systems. Metasploit offers a vast database of known vulnerabilities,Continue reading “Metasploit – Explained In 200 Words”
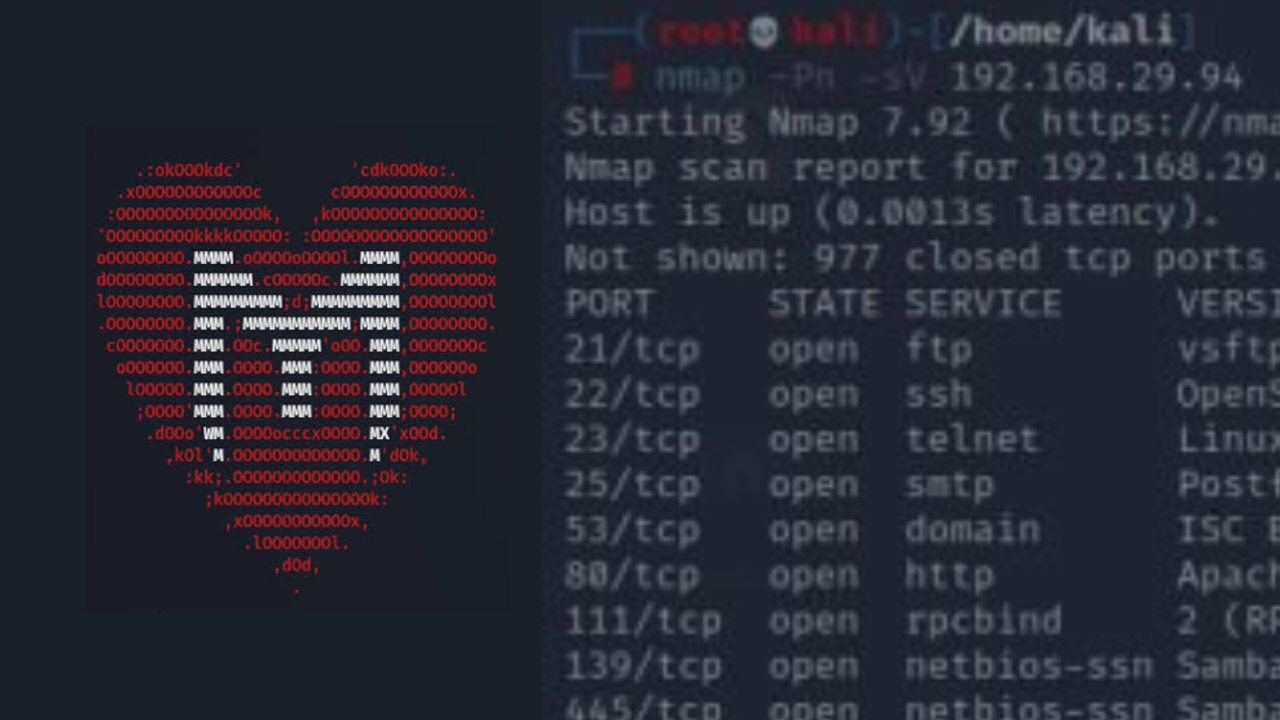
Nmap – Explained In 200 Words
Nmap, short for Network Mapper, is a free and open-source network scanning tool used for discovering hosts and services on a computer network and evaluating their security posture. Developed by Gordon Lyon in 1997, Nmap has become one of the most widely used network exploration and security auditing tools. Nmap utilizes raw IP packets toContinue reading “Nmap – Explained In 200 Words”
Git – Explained In 200 Words
Git is a distributed version control system used for tracking changes in source code during software development. Created by Linus Torvalds in 2005, Git was designed to handle the demands of the Linux kernel development process. It quickly gained popularity due to its speed, efficiency, and powerful branching and merging capabilities. Git allows developers toContinue reading “Git – Explained In 200 Words”
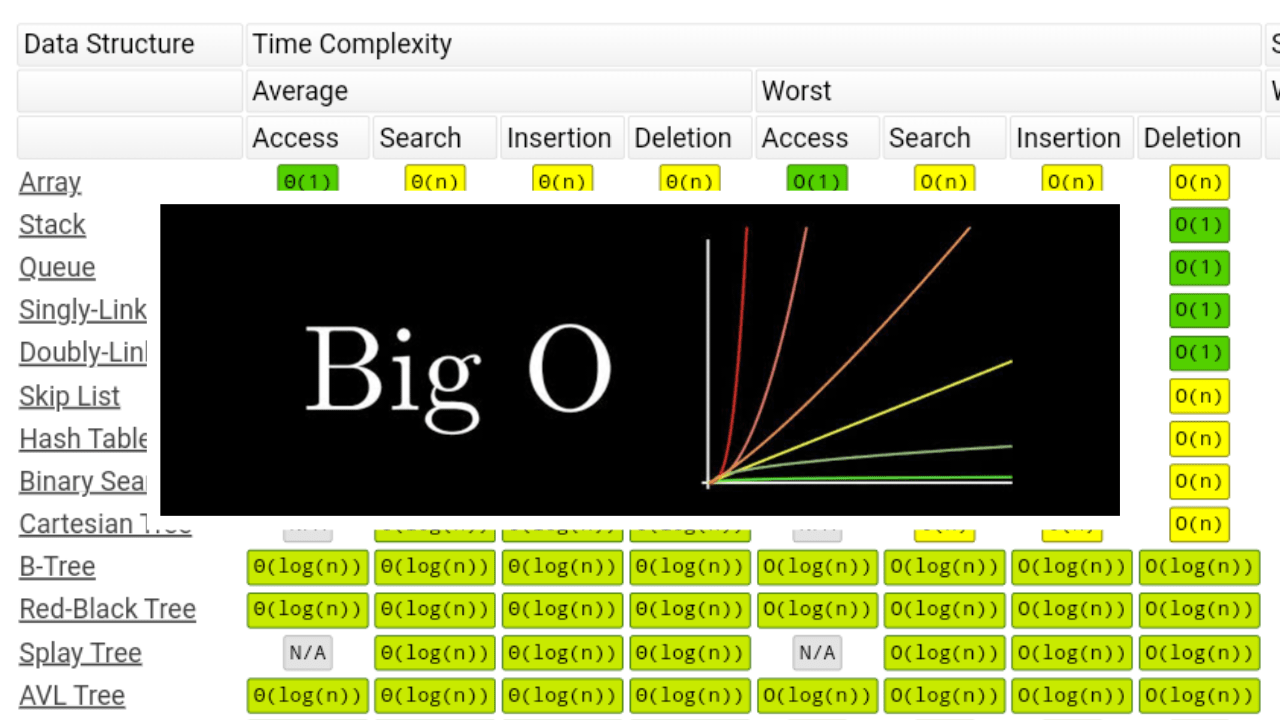
Big O Notation – Explained In 200 Words
Big O notation is a mathematical concept used in computer science to analyze algorithm efficiency. It originated in mathematics but gained prominence in computer science in the 1970s, with Donald Knuth’s work. It simplifies the comparison of algorithms by quantifying their worst-case performance as input size increases. For instance, consider linear search (O(n)) versus binaryContinue reading “Big O Notation – Explained In 200 Words”
DDoS Attack – Explained In 200 Word
The term “DDoS” stands for Distributed Denial of Service, a malicious tactic aiming to disrupt online services by overwhelming their servers with a flood of traffic. The first documented DDoS attack took place in 1999, orchestrated by hacker Michael Calce, alias “Mafiaboy,” who targeted major websites like Yahoo, eBay, and Amazon. Unlike traditional DoS attacks,Continue reading “DDoS Attack – Explained In 200 Word”
GPT – Explained in 200 Words
GPT (Generative Pre-trained Transformer) is a cutting-edge artificial intelligence model developed by OpenAI. It belongs to the Transformer architecture family and is trained on vast amounts of text data to understand and generate human-like text. GPT models are known for their ability to generate coherent and contextually relevant text across various tasks, including language translation,Continue reading “GPT – Explained in 200 Words”
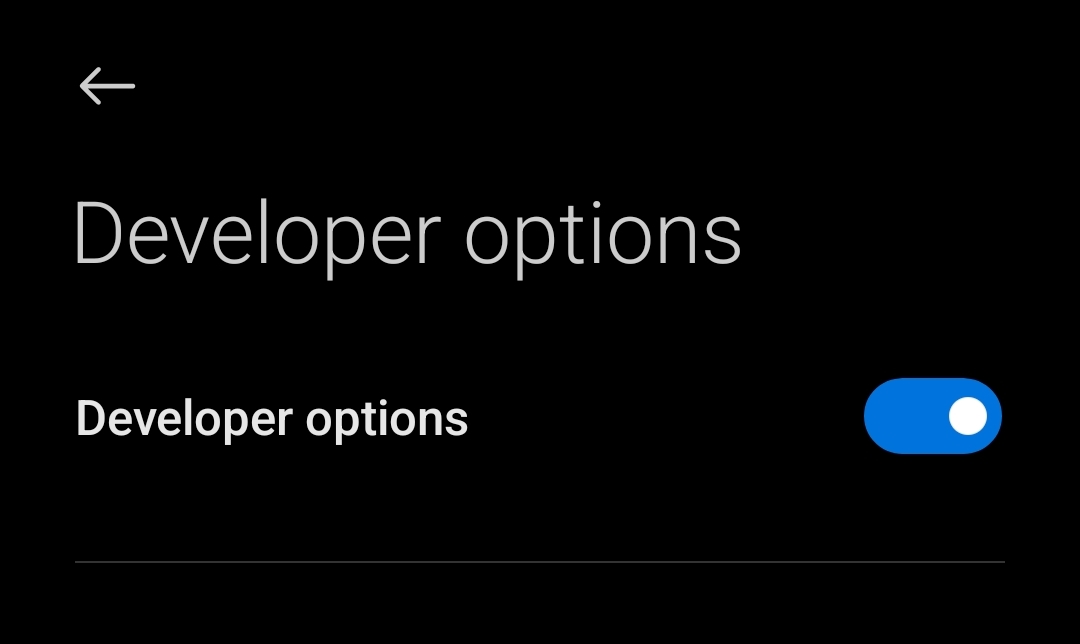
Secret Setting HIDDEN in your phone – Enable ” Developer Mode ” In Android
There is a hidden built-in feature which lets android developers to modify android system or make compatible android app. Lets follow the steps below to enable this function in your android phone – Step – 1 : Go To ” Settings” App Step -2 : Find The ” Build Number ” or ” MIUI VersionContinue reading “Secret Setting HIDDEN in your phone – Enable ” Developer Mode ” In Android”
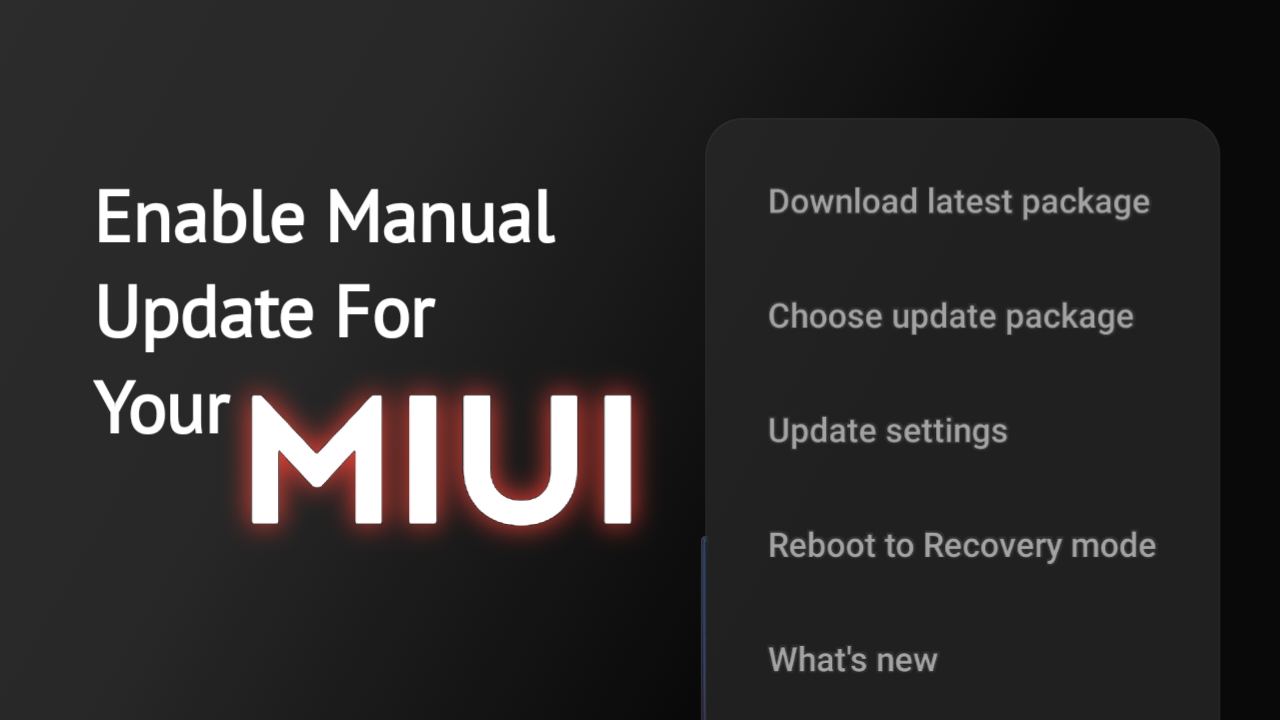
Enable ” Addition Update Feature ” On Any Xiaomi
Xiaomi has a bad history of giving bad rom service for the past few years. Some of them disabled important features, some drains battery really quickly, some created display issue. If you have one of this, you might thought of reversing to previous version. There are ways you can change rom but one of theContinue reading “Enable ” Addition Update Feature ” On Any Xiaomi”