Ethical hacking, rooted in the 1960s, evolved alongside the growth of computer networks and cyber threats. Early practitioners, dubbed “white-hat hackers,” pioneered techniques to secure systems. In the 1970s and 1980s, ethical hacking gained prominence as organizations sought ways to safeguard their digital assets. The Computer Fraud and Abuse Act of 1986 in the UnitedContinue reading “Ethical Hacking – Explained In 200 Words”
Tag Archives: ethical hacking
Metasploit – Explained In 200 Words
Metasploit is an open-source penetration testing framework used for developing, testing, and executing exploit code against remote targets. Developed by H.D. Moore in 2003, Metasploit provides a comprehensive suite of tools and utilities for security professionals and researchers to assess and exploit vulnerabilities in networks and systems. Metasploit offers a vast database of known vulnerabilities,Continue reading “Metasploit – Explained In 200 Words”
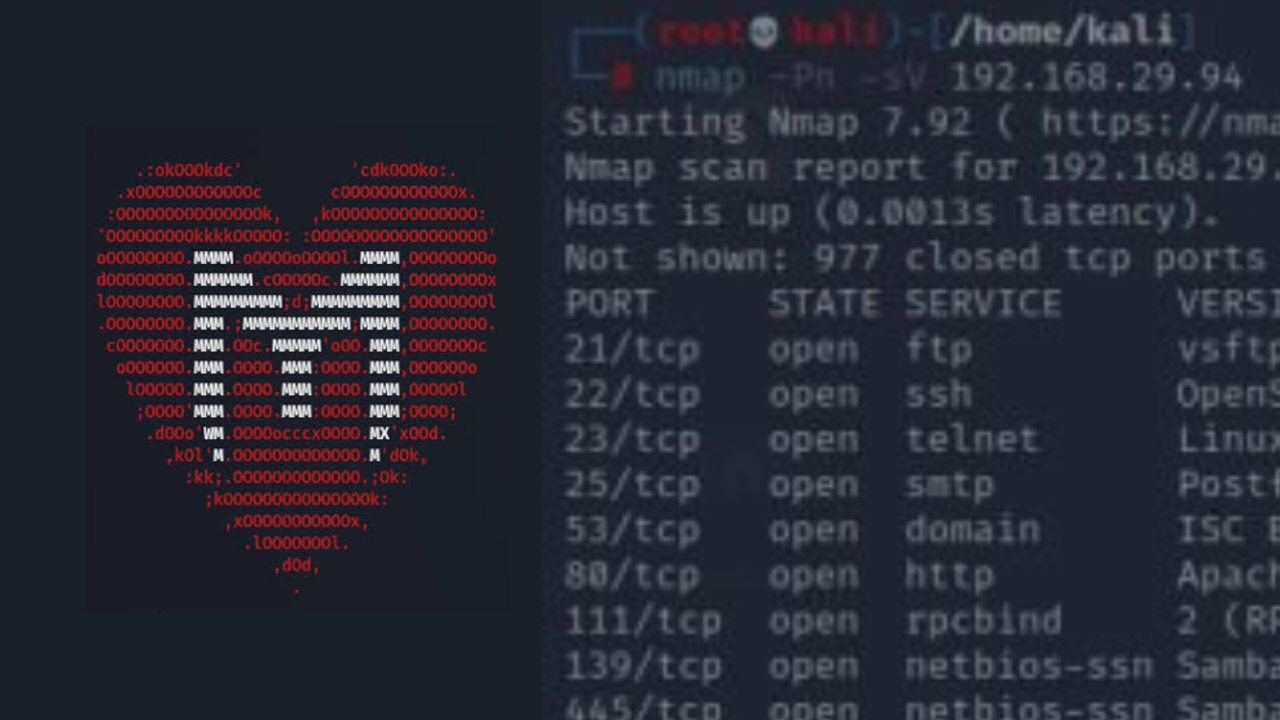
Nmap – Explained In 200 Words
Nmap, short for Network Mapper, is a free and open-source network scanning tool used for discovering hosts and services on a computer network and evaluating their security posture. Developed by Gordon Lyon in 1997, Nmap has become one of the most widely used network exploration and security auditing tools. Nmap utilizes raw IP packets toContinue reading “Nmap – Explained In 200 Words”